GETTING STARTED
INSURANCE COMPANY STORIES
SERVICE PARTNER STORIES
API BASICS
API ENDPOINTS
COMPONENTS
LEGACY
Azure AD federation
- Open Azure AD in Azure Portal
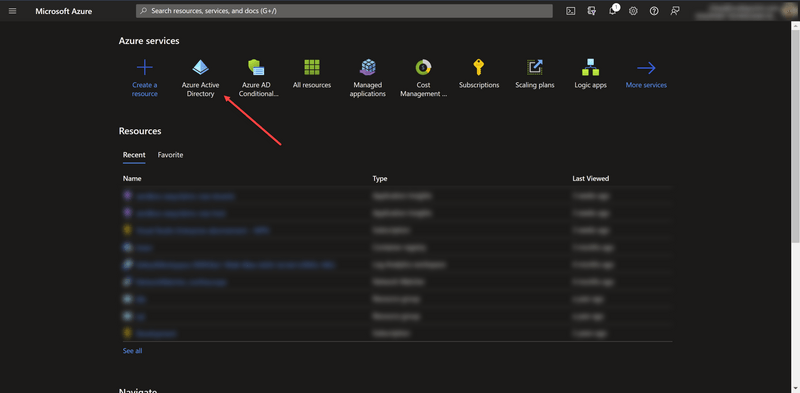
- Go to Enterprise applications
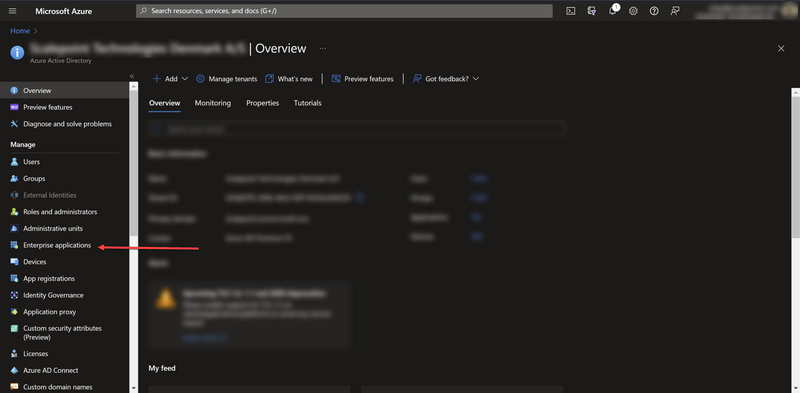
- Add new Enterprise applications
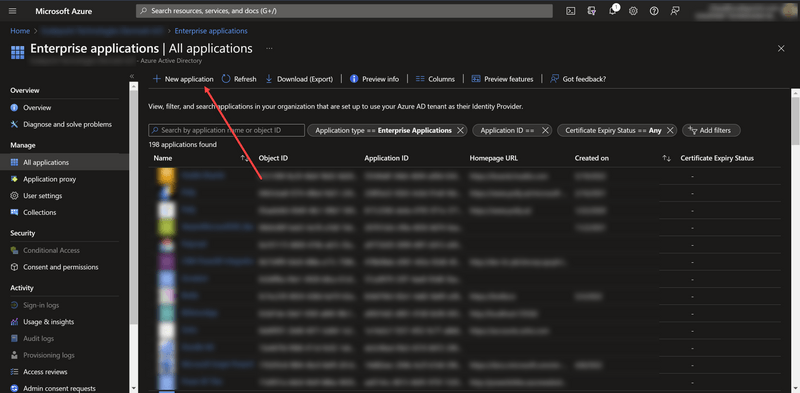
- Create your own Enterprise applications
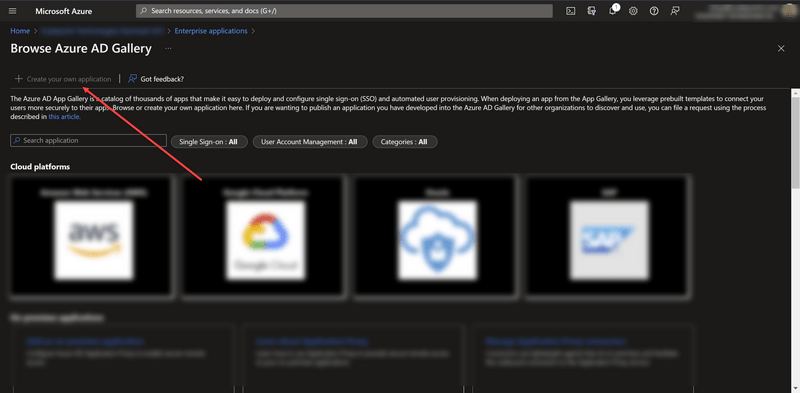
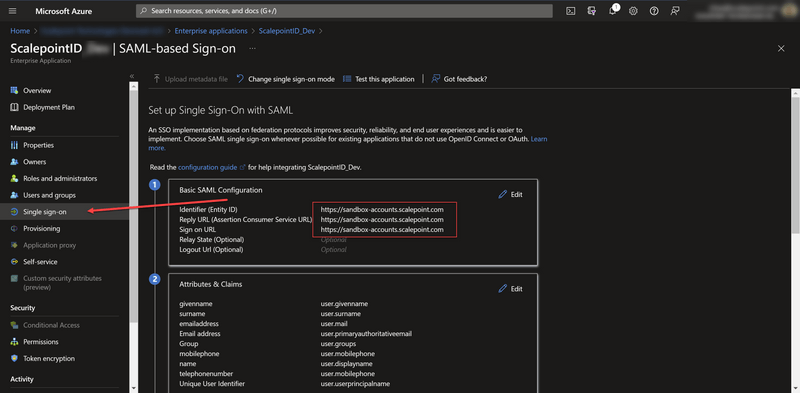
- Go to "Single Sign-On" and set Identifier, Reply URL and Sign on URL to a desired ScalepointID instance.
The instance is normally one of the following:
- Sandbox: https://sandbox-accounts.scalepoint.com
- Production: https://accounts.scalepoint.com
-
Claim mapping in Azure AD
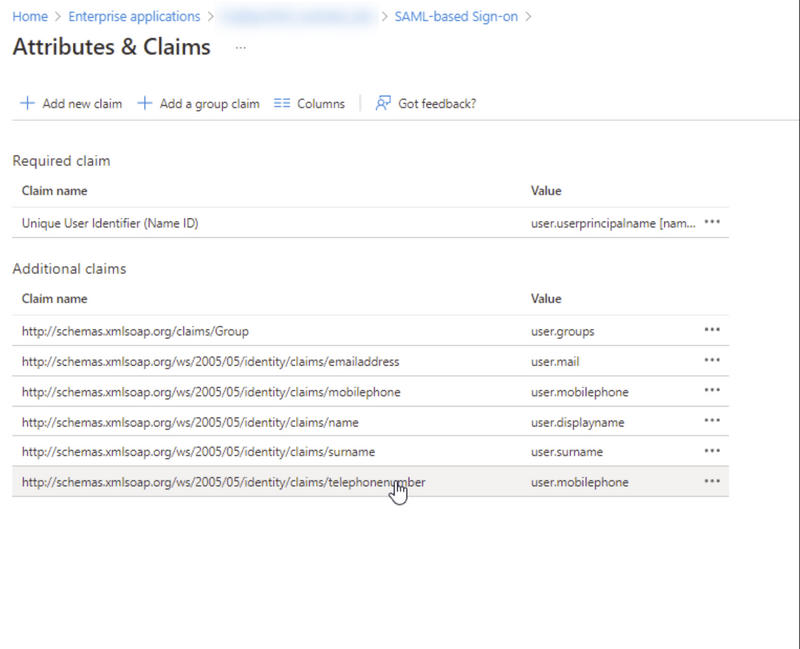
ScalepointID expects the following claims to be passed in SAML token. The "Azure AD property" is the recommended value, but it can differ depending on configuration. Please mind the "Value Example" to check if the value is correct.
| Name | Claim Type | Azure AD property | Value Example | Comment |
|---|---|---|---|---|
| Name | http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name | user.displayname | John Doe | |
| http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress | user.mail | john@example.com | ||
| Mobile phone number | http://schemas.xmlsoap.org/ws/2005/05/identity/claims/mobilephone | user.mobilephone | +4522334455 | |
| Phone number | http://schemas.xmlsoap.org/ws/2005/05/identity/claims/telephonenumber | user.telephonenumber | +4533442211 | |
| Department | http://schemas.xmlsoap.org/ws/2005/05/identity/claims/departmentnumber | user.groups | SCALEPOINT_MOTOR_CLAIMS | Claim is optional. Can be used to pass the "Department" group value if it's not possible to pass in the "Group" claim |
| Group | http://schemas.xmlsoap.org/claims/Group | user.groups | SCALEPOINT_CLAIMHANDLER | Can be used to pass both Security and Department groups in ScalepointID |
-
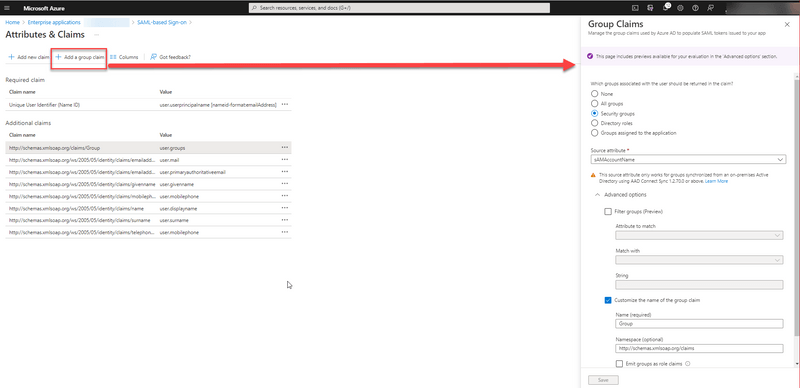
Group claims configuration
Group claim can be configured by pressing the "Add a group claim" button. The application should be configured the way that all the groups needed for ScalepointID are passed in the custom group claim "http://schemas.xmlsoap.org/claims/Group". The administrator should pay attention that the groups which are not needed for ScalepointID are not passed. If any extra groups are passed to ScalepointID - they will be ignored, but there can be an issue with SAML token size in browser if there is too many groups. So it is recommended to only pass the groups which are used in ScalepointID. It can be achieved by setting the different "Which groups associated with the user should be returned in the claim" and "Source attribute". It's also helpful to use the "Regex pattern" field to filter out the groups which are not needed.
-
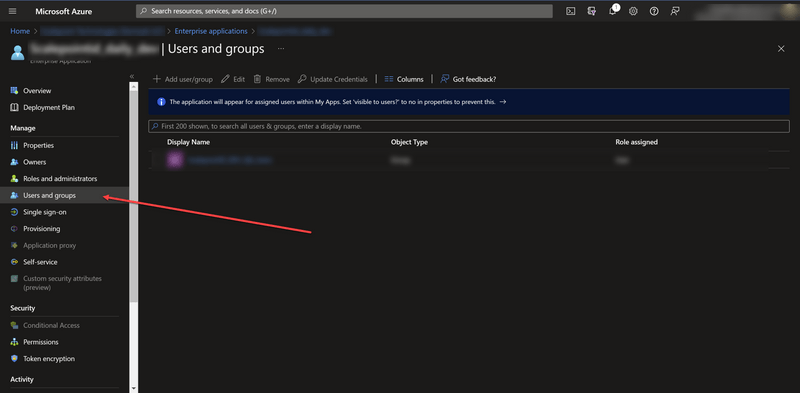
Users and Groups
On the "Users and Groups" menu specify who should have access to the application. It's recommended to give access to all users who can potentially work with Scalepoint applications. It is recommended to use a group or a dynamic group so it's unnecessary to add every single user added from AD.