GETTING STARTED
INSURANCE COMPANY STORIES
SERVICE PARTNER STORIES
API BASICS
API ENDPOINTS
COMPONENTS
LEGACY
Entra ID federation
Scalepoint now supports OIDC federation to Entra ID, which is a recommended option for enterprise customers who support it.
Install the Scalepoint enterprise app
There are two separate Entra ID apps available for production and sandbox environments: "Scalepoint (production)" and "Scalepoint (sandbox)", respectively. You will likely want both configured. Start with sandbox and, once verified, configure production accordingly.
There are several ways to install the application: via Microsoft Entra Gallery, via a consent link, or by signing in with the user who has administrative privileges in Entra ID.
Consent link
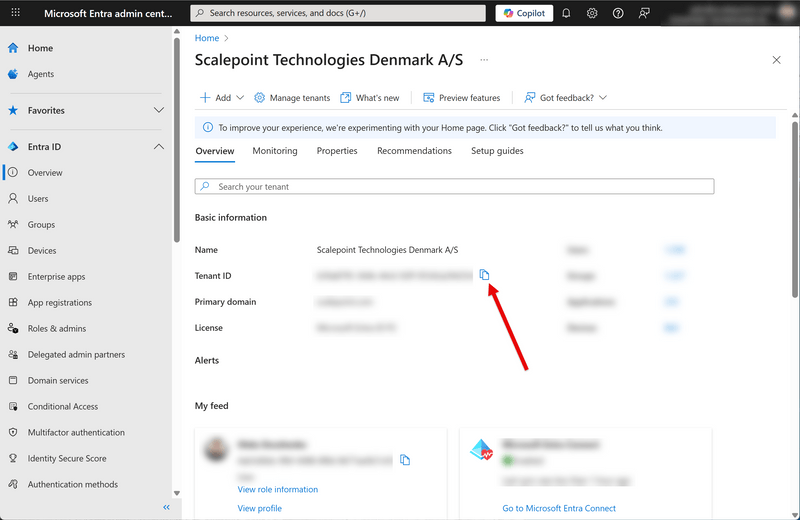
Another option for installing the app is to use a consent link. The format of the consent link differs between environments: https://login.microsoftonline.com/{tenant-id}/adminconsent?client_id=8ac362f7-bb33-41e7-8a32-c2c3b549b728 (sandbox) or https://login.microsoftonline.com/{tenant-id}/adminconsent?client_id=11b2becd-c3b0-42da-a037-63a53dd41434 (production), where {tenant-id} is your organization's tenant ID in Entra.
To get it, go to your Entra ID >> Overview and copy your Tenant ID value. Please provide Scalepoint with this value. It is needed to associate your organization's Entra ID tenant with the tenant in Scalepoint ID.
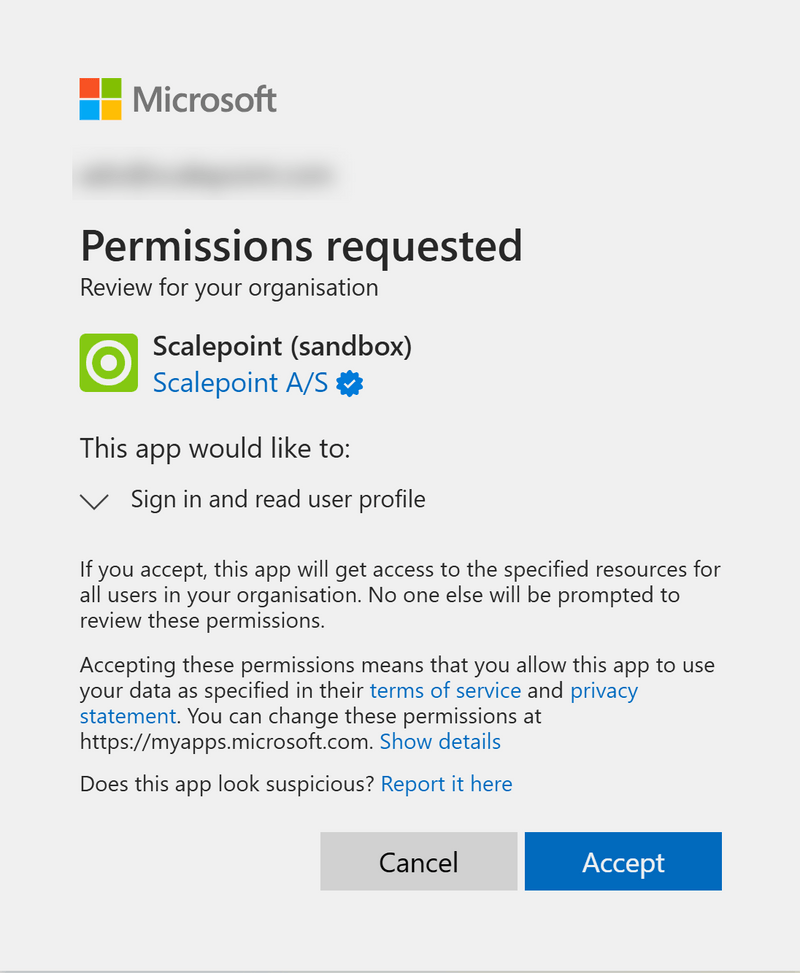
After opening the link, you will see a consent screen. As soon as you accept it, the application will appear in your organization's Enterprise Apps menu.
Signing in
You may achieve the same if you log in to Scalepoint by using the user with administrative privileges in Entra. You will see the same consent screen as in the previous option.
User attribute and claim mapping
This mapping is pre-configured out of the box and does not require additional configuration.
User attributes
Scalepoint uses the following user data: Display name, Job title, User principal name, Department, Mobile phone, Email, Account enabled, and the groups the user belongs to.
Group mapping
In order to map a user group, you need the group alias in Scalepoint to match the Entra group's Object ID.
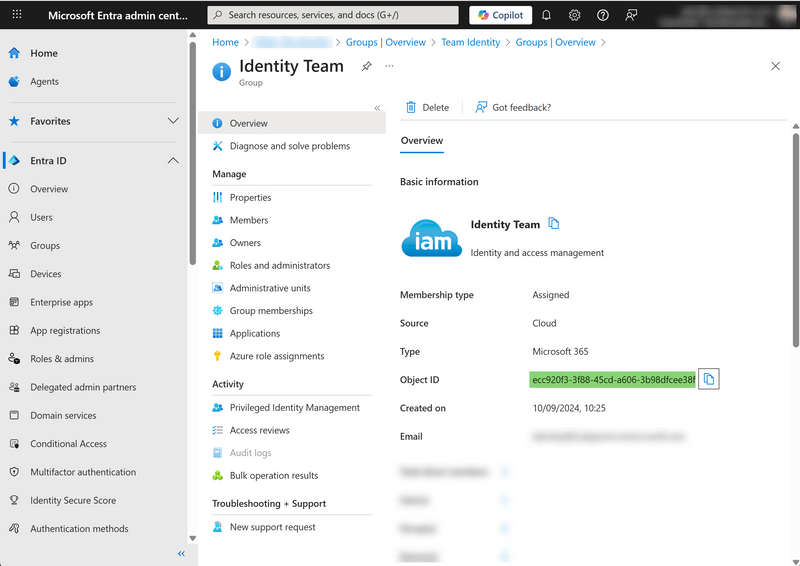
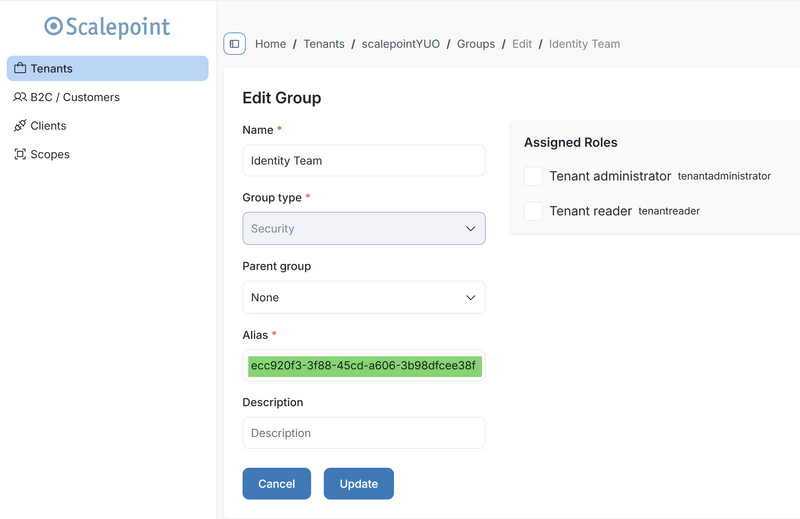
Department mapping
Department groups are automatically created in Scalepoint ID based on department attribute value and user is automatically assigned to that department.
Note: At the moment, these departments are not automatically created in products. This means that in ClaimsCORE & HUB, departments and user pools need to be manually created with correct External IDs matching the original string.
App roles
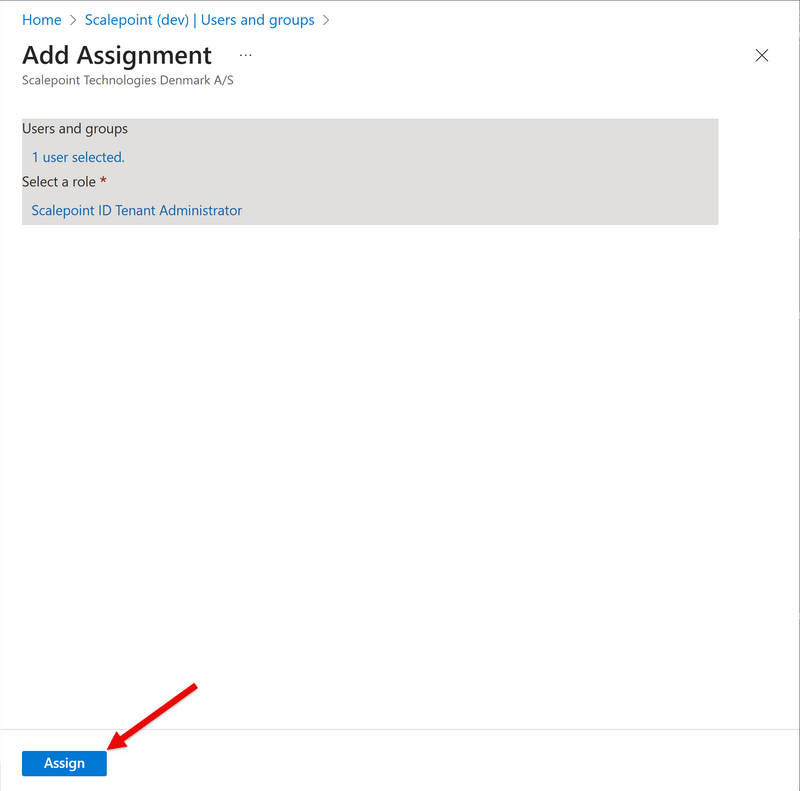
There is a new way of providing your users with privileged access. For that to work, go to "Enterprise apps", find the Scalepoint app, select "Users and groups", click "Add user/group", and assign the user to one of the roles. The selected user will have corresponding access to Scalepoint now. Only two predefined privileged roles are supported at the moment: Scalepoint ID Tenant Reader and Scalepoint ID Tenant Administrator, plus Custom access used for all other assignments. Tip: You can assign eligible assignment groups to these privileged roles to utilize Entra's Privileged Identity Management features.
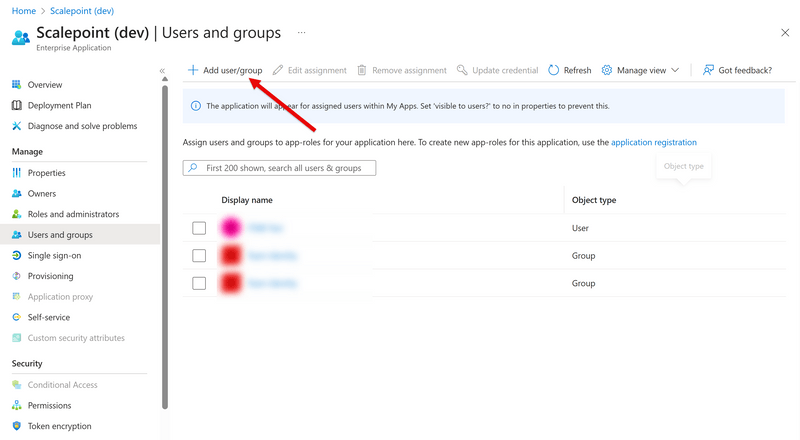
User group filtering
User's groups in your Entra ID are not visible to Scalepoint automatically. You have to assign any groups that you want to make visible in the Enterprise app's "Users and groups". Repeat the user assignment steps from the App roles section, but choose application role Custom access to later assign product specific roles and permissions inside Scalepoint ID.
Optional user assignment
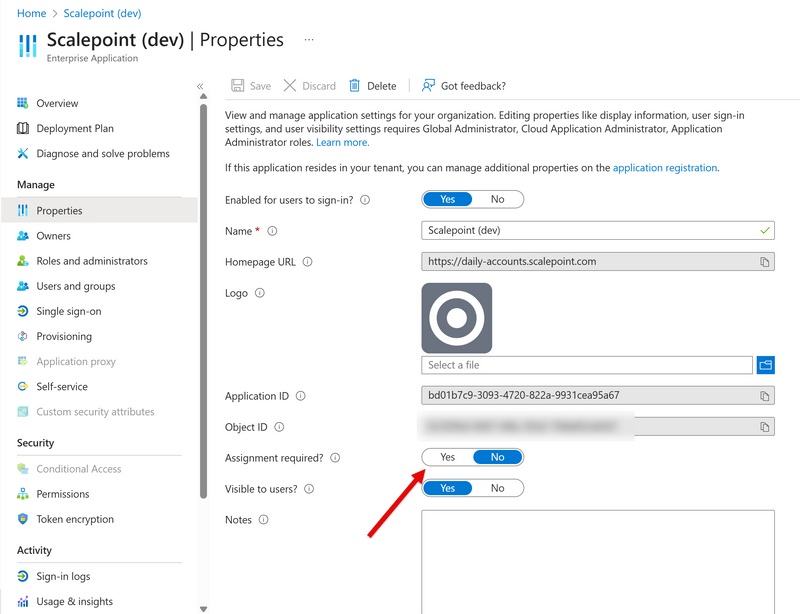
You can control which users can sign in to Scalepoint by using the "Assignment required?" switch on Enterprise app "Properties" tab.
Conditional access and multi-factor authentication
When using Entra ID single sign-on to Scalepoint, you can use Conditional Access features in Entra ID to implement additional protection measures to enforce, for example:
- Multi-factor authentication
- Device-based conditional access with Intune
- Block access by location
We highly recommend to implement multi-factor authentication on Entra ID side. This approach provides the best user experience, minimal management overhead, and highest security since no additional authenticators need to be managed.
User and group provisioning
This functionality is in development now.